Amid this global health crisis caused by the spread of COVID-19, it is vital to realize that the coronavirus is not the only threat out there that we need to be actively protecting ourselves against. The massive surge of people working from home has introduced ample opportunity for fraudsters to hack into secure devices and networks, exposing private information and exploiting vulnerable individuals and businesses. A cyber attack has the potential to financially devastate those who fall victim. It is absolutely imperative to be informed and prepared in the event of a hack. For additional information on Cyber Insurance, check out our Cyber Liability Insurance page.
RECENT METHODS OF ATTACK
Unfortunately, the pandemic has inspired cyber criminals to profit off of global fear. The number of phishing and scam websites themed around the coronavirus pandemic is growing exponentially. In fact, the number of cyber attacks related to the coronavirus is possibly the largest ever recognized around a single theme.
Several domain names have been registered under the guise of coronavirus keywords and they can be used to infect users with malware. Hijacked D.N.S. settings display an alert for a bogus COVID-19 information app that claims to be produced by the World Health Organization. If a user clicks on the alert and launches the app, the malware attempts to steal the following information from the user’s PC:
- Browser cookies
- Browser history
- Saved login credentials
- Browser payment information
- Cryptocurrency wallets
- Text files
- Browser form autofill information
- 2FA authenticator databases
- A screenshot of your desktop at the time of infection
The digital perpetrator will not leave any valuable information untouched.
Cyber criminals are even going as far as targeting places like hospitals and exploiting them with the installation of ransomware. The expectation is that the urgent need for system functionality will push administrators to quickly pay the ransom demanded.
From corporations and mom-and-pop businesses to strikes on individuals, no one is exempt from these types of attacks. However, knowledge is the best form of armor, and if you know what to look for, you will be able to put up a strong defense against these types of cyber torpedoes.
CYBER RISKS AND WHAT CLUES TO LOOK FOR
The three major cyber risks that individuals and businesses should be aware of right now are social engineering, phishing, and ransomware.
Social Engineering
Social engineering is the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. This form of deception has many faces, but it usually takes place by way of phishing emails or phone calls.
Phishing
Phishing is the fraudulent practice of sending emails to be from reputable companies in order to encourage individuals to reveal personal information such as account details, passwords, and credit card numbers. To spot a phishing email, keep your eyes peeled for the following clues:
- Sender email address-if it looks wonky with strange punctuation, random letters and numbers, or the email address just doesn’t look familiar, it may be falsified.
- Destination email address
- Urgent or time sensitive response requested
- Embedded links or attachments
- Asking for confidential information
- Asking for payment information
If you receive an email requesting you to click on a link to reset your password, verify your account or enter banking information – MAKE SURE you requested this communication first before you click or enter anything. Many businesses and institutions have strict rules about how they digitally communicate with you and will openly publish the fact that they will never ask you for personal or account information via email.
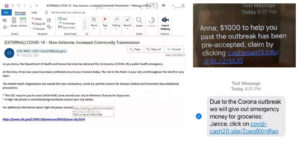
Phishing Examples
Ransomware
Ransomware is malware that infects computers and restricts access to files. In order to avoid permanent data destruction, a ransom must be paid. This is currently the fastest growing form of cyber crime. The culprit can attain wealth quickly and with little hassle.
How a ransomware attack transpires:
- The intruder will send an email containing a link or file that the user clicks on
- Once the link or file is clicked, the ransomware will seep into the workstation
- The ransomware then encrypts network data so it cannot be accessed by the organization until the demanded ransom is paid
- Once the ransom is paid, the intruder unlocks the data for the organization. However, this does not always happen.
To mitigate the risk of cyber infection, be vigilant when reading emails and answering phone calls. Never give out personal or business information and do not engage with unfamiliar links or files. Most importantly, make sure that you have protection in place and a plan of action should you discover that your network has been invaded.
STAY PROTECTED
No person or business wants to subject themselves to a cyberattack. The best thing that you and your business can do to avoid such a situation is to be proactive. Make sure that you have implemented several forms of digital protection.
5 Easy Steps to Securing Your Home Office
Since most of us are currently working from home, it makes for a great starting point. You should prioritize your home office in your defense against possible cyber onslaught. Follow these 5 easy steps to secure your WFH devices!
Free Guide to Securing Your Home Office
Invest in Cyber Insurance
Choose a cyber insurance provider that offers premium coverage. Here at Camargo, we recommend industry leader Evolve MGA. Evolve offers a 24/7 cyber incident response team with immediate assistance if your network is breached. With every Evolve policy, you will also benefit from CyberRiskAware. This free tool creates fake phishing email campaigns that are sent to staff members. If a staff member opens the email and clicks the phishing link, they will see an educational video. Human error is currently the highest cause of cyber related claims. Training tools like CyberRiskAware are imperative.
For more information, Camargo has access to industry leader Evolve MGA for customized Cyber Insurance for your businesses needs. Connect with us to get a free risk assessment and fast quote to protect your business.
Multifactor Authentication
Multifactor Authentication, also known as MFA or 2FA, is one of the most successful security methods. Some complex attacks begin when a hacker breaches a network and gains access to email accounts. This access shows them how the business interacts. The hacker then creates an email account resembling an email one may receive from an employee, senior officer, etc. This can easily dupe an individual into giving out private information.
MFA is recommended when logging into email accounts or applications that require a user ID and password. It sends an authorization code to the user’s cell phone that confirms who is logging into the account.
Be sure to enable MFA on all of your online accounts which offer this security measure. Accounts secured with MFA protocols include cloud-based software, email servers and banking or investment portals.
Call Back Procedure
A call back procedure is one of the most impactful practices that a business can implement, especially if you are a business that works with the transferring of funds. Before processing any wire transfer or ACH, call the source that is requesting the funds directly to confirm that all of the information is correct and that they are expecting a deposit. Do not obtain the telephone number from the email or the letter that is requesting the funds. Find the phone number through an internal source or a web search that you conduct yourself.
2-Person Authorization
This type of protection is applicable in any industry but especially useful if you transfer large amounts of money. We recommend multiple people reviewing and approving large monetary transfers (preferably senior employees.)
Additional Forms of Protection
- Use a password manager like LastPass to generate and store unique, intricate passwords and NEVER use the same password twice.
- Use a passcode lock on your electronic devices
- Turn on automatic system updates on your electronic devices
- Make sure your desktop web browser utilizes automatic security updates
- Do not share credentials or permissions for any network or cloud accounts
- Store all corporate data in designated locations
- Be aware of malicious websites, links, and files
Cyber protection is essential to individual and business security in today’s workforce climate. Take some time to get familiar with your digital security obligations while you’re working from home. You’ll have an impenetrable shield to safeguard your information and your investments. Camargo Insurance has dedicated agents who can assist you in properly assessing your risk and getting the right protection in place, chat with us to discuss next steps!
Subscribe to Our Blog
Our Recent Posts
-
When it comes to coverage - go beyond the obvious. October 16, 2024
-
Beware of Roofing Scams After a Storm October 9, 2024
-
When you should (and shouldn't) file a claim. October 1, 2024
-
Life Insurance: Why It's Crucial for Personal and Business Insurance September 11, 2024
-
Navigating the Challenges of the Insurance Hard Market August 7, 2024
